Almost Normal
The latest edition of Art Dubai Digital looks more like a regular art fair than its predecessors, but still has subversive and experimental work.
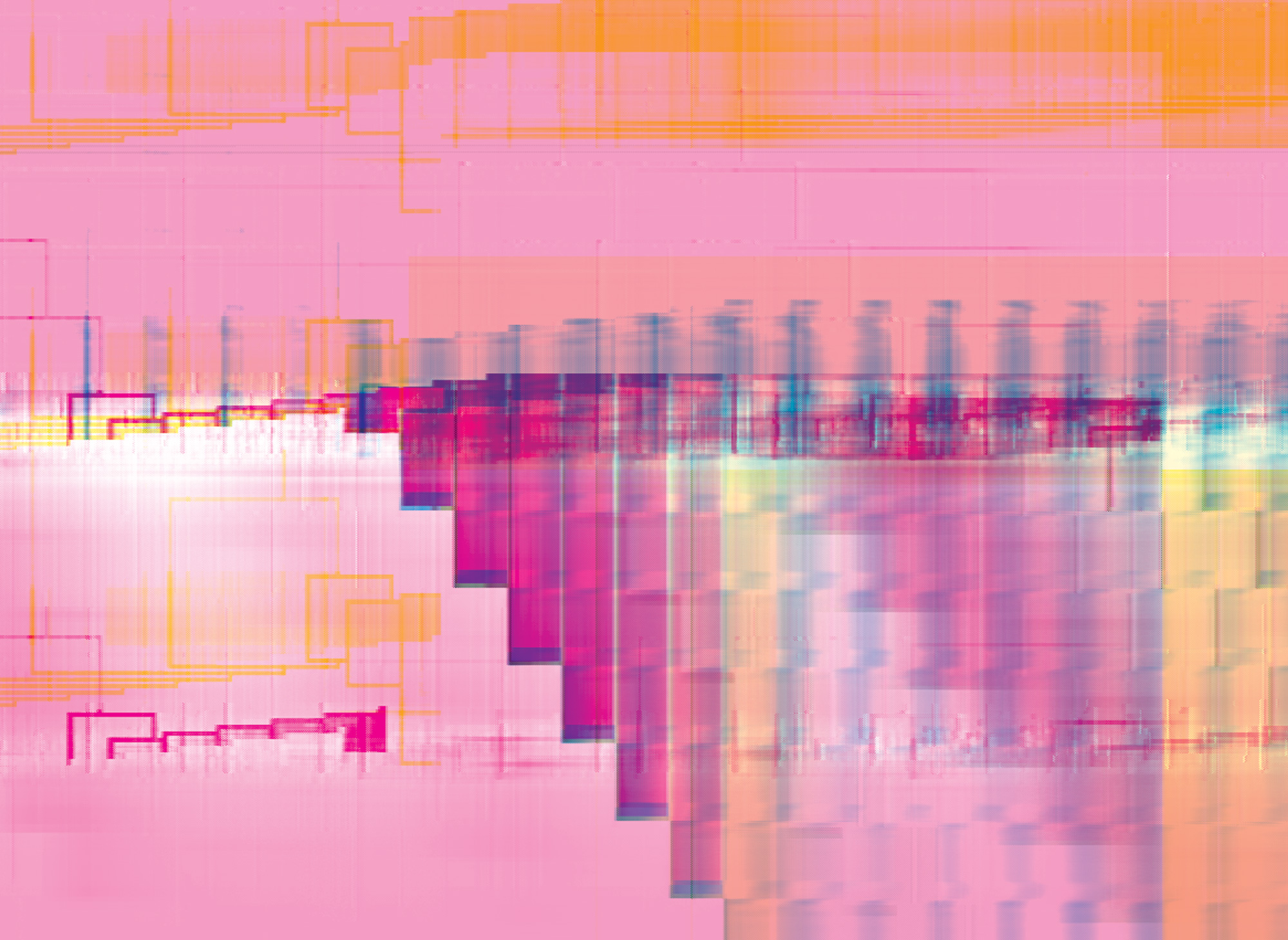
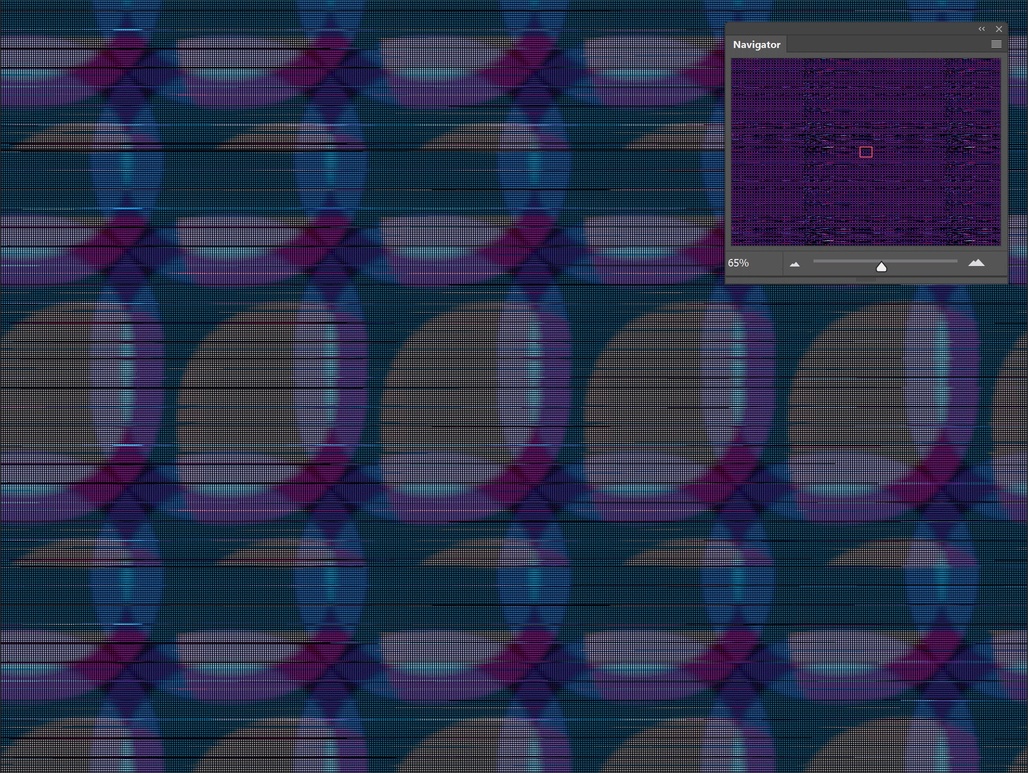
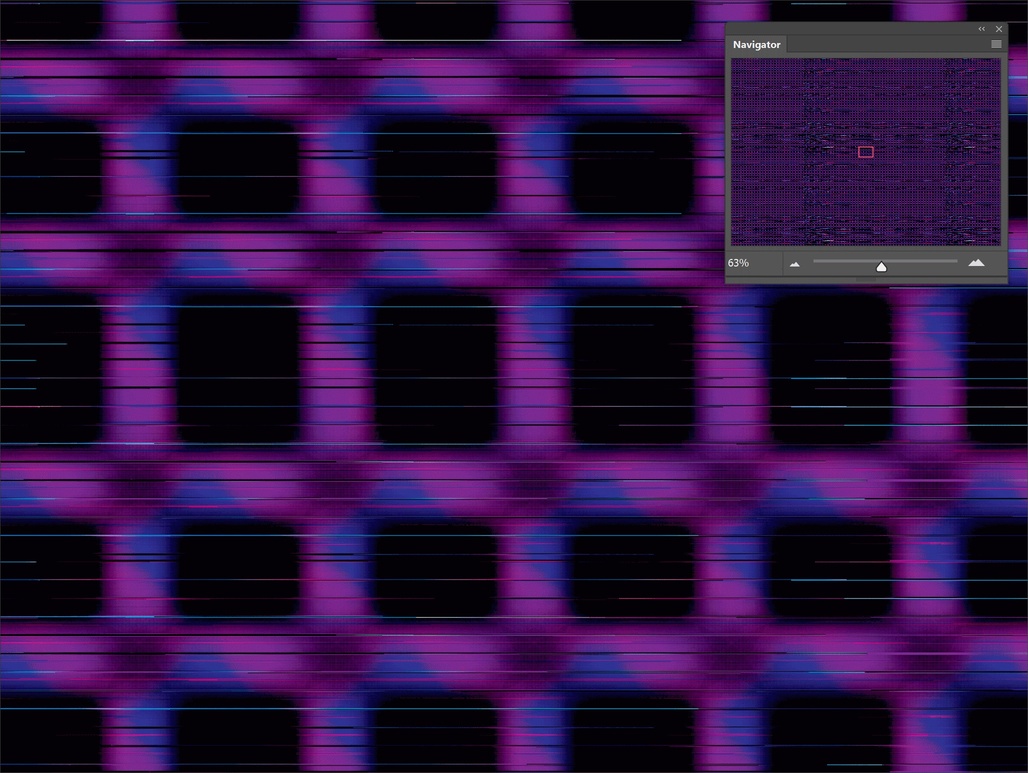
Code either works or it doesn’t. Of the many binaries that glitch art breaks, that is the first. Often in glitch practice, systems fail to fully fail, producing some kind of output—but one far from what they were designed to do. When existing algorithms are hijacked to provoke new behaviors, this is often done with no code, manipulating the algorithm by giving it nonstandard input or context. You could call this process “algorithmic glitch.”
Algorithmic glitch is one technique of many in glitch art, ranging from the spontaneous capture of crashed-out digital displays to a host of filters and apps that very consciously “break” photographic images to expose their digital viscera. The algorithmic glitch is not the writing of algorithms to apply glitch-like effects but rather the manipulation of found algorithms, as artists hijack them to provoke new behaviors. In estranging the normative functions of code, this practice resembles hacker folk arts such as the self-consciously experimental practices of esoteric programming languages, otherwise known as esolangs. Esolangs offer strange syntaxes and twisted logic in complete opposition to the clarity of conventional programming languages. They are puzzle languages that challenge programmers’ skill, or pose questions about how code can be written, what computers are for, who they are for, and how code is commercialized. While esolangs and algorithmic glitch take different forms, their shared ethos of algorithmic subversion re-wilds the algorithm, makes it inscrutable, and distances its behavior from the source code that set it in motion.

In the early algorithmic glitch practice of databending, the binary data of audio or image files is manipulated, resulting in glitch artifacts: wavy red, green, and blue ghost images, or crunchy, dislodged pixels scattered across an image. (The term “databending” is a reference to the DIY practice of circuit bending, where electronic toys are rewired to create new musical instruments.) This practice perhaps reached its best-known culmination in Rosa Menkman’s Vernacular of File Formats (2009), where the same haunting image is glitched serially across many file formats (included some invented by Kim Asendorf for the sole purpose of glitching). But this practice can’t be understood in terms of data alone. Data is an animate form, blossoming into artifacts of distortion and abstraction when interpreted, decompressed, rendered to the screen. “Bad data” is bad input to an algorithm, invoking behavior contrary to the algorithm’s design. While much of the language we use for glitch refers to data—datamoshing, data corruption, signal and noise—we only see the results when this data is instrumentalized through the algorithm.
Glitch, then, introduced something new: a form of pseudo-programming without code. The algorithm can remain a black box, stuck in proprietary software whose code we can’t read. In algorithmic glitch, the process is whatever the code can be used for: the intent for the algorithm (by its programmer) and its side effects are held in equal regard. We learn the potential of an algorithm through use, by testing its boundaries. In Vernacular of File Formats, algorithms of decompression and rendering were altered mostly through direct manipulation of the data. In my series The Unprintable (2016–17), image patterns are designed contrary to interpolation algorithms, breaking the way image pixels map to the screen. This process results in digital images with no consistent digital representation, changing dramatically as one zooms in or out. The result is so unstable that the work can’t be shown online: videos of the work can’t be compressed without turning into static.
This process of discovery of an algorithm’s use is reminiscent of the work of the esoprogrammer, who writes esoteric languages that break from conventional computing.
This process of discovery of an algorithm’s use is reminiscent of the work of the esoprogrammer, who writes esoteric languages that break from conventional computing. Languages like SUBLEQ or Malbolge have mazes of self-referential programs, where changing one symbol might alter commands across the program—much like how glitch artists, altering a single byte in a compressed file, shatter the image it holds. Malbolge programs, which run in a loop, encrypt themselves as they run, so each command does something different on the next iteration. It is far too complex for a programmer to keep in their head. The designer of Malbolge, or any other esoteric language, sets its constraints but can’t fully understand the logic of the system they define alone. Other programmers come to the language with their own agendas, their own coding styles, and push the limits of the language. They make discoveries its designer could not foresee. Likewise, in the hands of a glitch artist, an algorithm’s original purpose is negated or superseded by the aims or accidental discoveries of the artist. Mainstream coding strives for a clarity of purpose, a unity of text and execution; its languages aim to be familiar and transparent. Esolangs create distance, where the text of code obscures its function, perhaps setting off a labyrinthine series of interpretations leading to computer action.
In the algorithmic glitch technique of sonification, we edit images while seeing them in translation as sound waves, unable to immediately experience their effects visually. We might guess that compressing time in an audio clip will condense the image, and it actually sometimes does, creating waves as the pixels misalign. Other effects, like delay (a type of echo), create drastically different visual outputs in reaction to apparently minor settings tweaks. The enigmatic algorithm goes hand-in-hand with the ambiguous control glitch artists exert. When working with sonification for my “Glitchometry” project (begun in 2011), I would often put the project aside for months or years at a time to forget the effect some algorithms have and get back to a place of pure exploration. Glitch abhors too much control: if a piece is too precise, too perfect, it smells wrong—it invokes the greater-glitch aesthetic that is now everywhere (in just the latest example, the cover for Naomi Klein’s latest book, Doppelganger, which features an apparently “glitchy” portrait of the author) but reads as not-quite-glitch. The joy of discovery in setting an errant algorithm in motion is lost when the artist knows where it will take them; images that lack the sense of chaos and spontaneity read as forced.
Glitch abhors too much control: if a piece is too precise, too perfect, it smells wrong.

Sonification is only possible because data has no inherent meaning to the machine; both image and sound are strings of numbers that can be directly manipulated. The interpretation of that data in one medium—as image or sound—can be assigned or retracted; the computer itself is, as computer scientist Alan Kay describes, a meta-medium. Esolangs use this multivalence of data, opening up multiple readings at once. In the Piet language, code takes the form of Mondrian-like blocks of color. In in:verse, the code is poetry; in Velato, the code is music. The programmer reads both meanings at once: the constraints of the language shape how it appears as image, poetry, music, and vice versa. This creation of a double meaning is a favorite technique of malware writers. Small shifts of opacity in individual pixels of an image, too small for most people to discern, can become a lexicon of malicious scripts, hidden in banner ads. The degree of an image’s opacity has a number, and numbers can be collected, translated, executed as code.
Algorithmic multivalence perhaps reaches its extreme in Yusuke Endoh’s 128-Language Quine Relay, which works in the gulf between machinic logic and human understanding to very different ends. Endoh, a contributor to the Ruby programming language, wrote a Ruby program that generates a Rust program that generates a Scala program that generates a Scheme program, working through the alphabet of languages, eventually wrapping around back to the Ruby program which spawned it. At any one time, the program has only the ability to achieve its next state, yet latently every program it will become is part of the accumulation of meanings in its text.

But perhaps most akin to glitch practice is the hypothetical esoteric language 90, posited by ais523 in 2015. Here, code is built entirely from rearranged, stolen algorithms. The language is named for the hexadecimal number representing the “no-op” (no operation) instruction, which does nothing. When run, the 90 language would manipulate a running process, swapping out its instructions for 90s. It inserts cavities, one by one, sculpting away behavior to reshape the program into something new. It could strip down, say, a running instance of Excel until all that is left is an animation, something entirely new assembled from the internal logic of the Excel process it disassembled.
The 90 language can only work by violating the concept of code isolation, which restricts software to only see and affect itself. The glitch, likewise, is defined as a behavior that refuses to act within the structure and hierarchy that contains it—bursting out into view, crashing, or misbehaving. Wendy Chun described the “bureaucracy in the machine,” a re-creation of a military command structure. When we write a script for Photoshop, we are the executive at the top of the chain, referring to only what we need: layers or palettes of images. Even if we wanted to, we could not specify technical details below, like how the physical machine should store the color red; that is hidden away behind the operating system, the Photoshop executable, other “layers” of code. Each layer is an abstraction, a metaphor, hiding details that should be irrelevant. A glitch is the hostile metaphor, the rupture across layers. Never a single text or top-down command, it occurs in the porousness between systems meant to be independent. The artists of algorithmic glitch work with algorithms as pure behavior, divorced from source texts, run in a context that brings systems together in unlikely combinations. Here, the algorithms never hold only one meaning; they become the place where many voices collide.
Daniel Temkin is a programmer, artist, and writer examining the clash between systemic logic and human irrationality.
